Defending against typosquatting requires constant vigilance and swift action. Learn the basics of this form of attack and defense strategies for SOCs and individuals.
Cybercrime tactics are evolving daily, and social engineering attacks remain the most-used attack vector by cybercriminals to infiltrate IT systems. According to the last Data Breach Investigations Report published by Verzion in 2023, 74% of data breaches involve human elements, including social engineering attacks, errors or misuse.
There are various types of social engineering attacks, all of which aim to manipulate human minds to cause them to engage in malicious behavior based on the attacker's objectives. In this article, I will discuss one type of social engineering, typosquatting.
What is typosquatting?
Typosquatting (also known as URL hijacking, domain mimicry or sting sites) is a type of SE attack that aims to mislead unsuspecting users into visiting malicious websites whose names are misspellings of legitimate websites. For example, threat actors may register a domain name called Yahooo.com that has the same look as the Yahoo! official website. Then they send the fake link to different users via phishing emails or malicious advertisements, or they wait for someone to visit it unknowingly; all this is to lead victims to sign into their real Yahoo! accounts using the fake website. The aim of hackers is to steal target users' account credentials, install malware on targets' computer devices or steal more information to conduct further attacks.
Internet users who type their website addresses directly in their web browser address bar are more susceptible to typosquatting attacks because they are likely to access some typosquatting websites inadvertently. The word "typo" at the beginning of typosquatting refers to users' small mistakes while typing their intended website addresses.
How typosquatting attacks are executed
A typosquatting attack involves a threat actor registering one or more domain names that are a misspelling of a popular website name. Generating misspelled domain names has become easier since the introduction of generative AI tools to the public. For example, we can use generative AI technology to get a list of all domain names that are very similar to a particular domain name.
For my experiment, I asked ChatGPT to give me 30 domain names similar or very close to authentic8.com (see Figure 1).
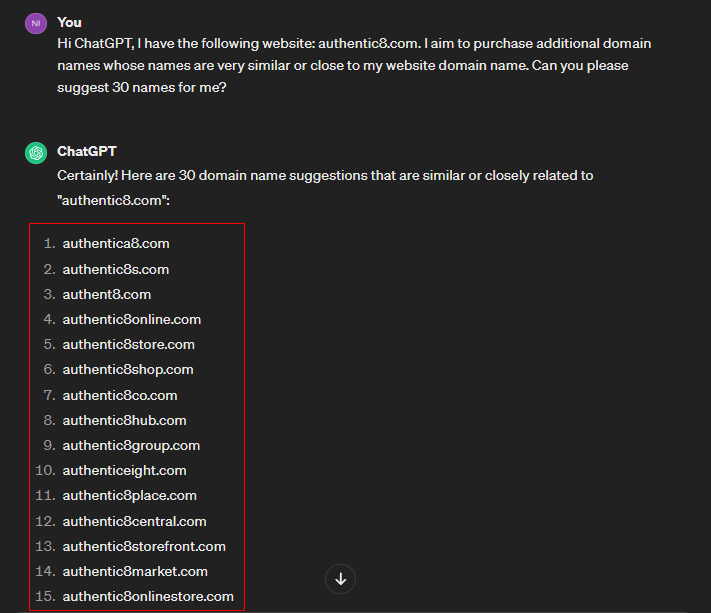
Figure 1 - We can abuse ChatGPT to suggest domain names for typosquatting
After checking the availability of these domain names, threat actors will register some of them and design a website that mimics the target one to lure the victims into using it.
You may wonder if mimicking a website requires some resources from attackers, such as money and expertise, but this is no longer an issue. For instance, cybercriminals can use a free automated tool such as HTTrack (see Figure 2) to get an offline version of any website and upload it to a hosting space to impersonate the legitimate website (see Figure 3).
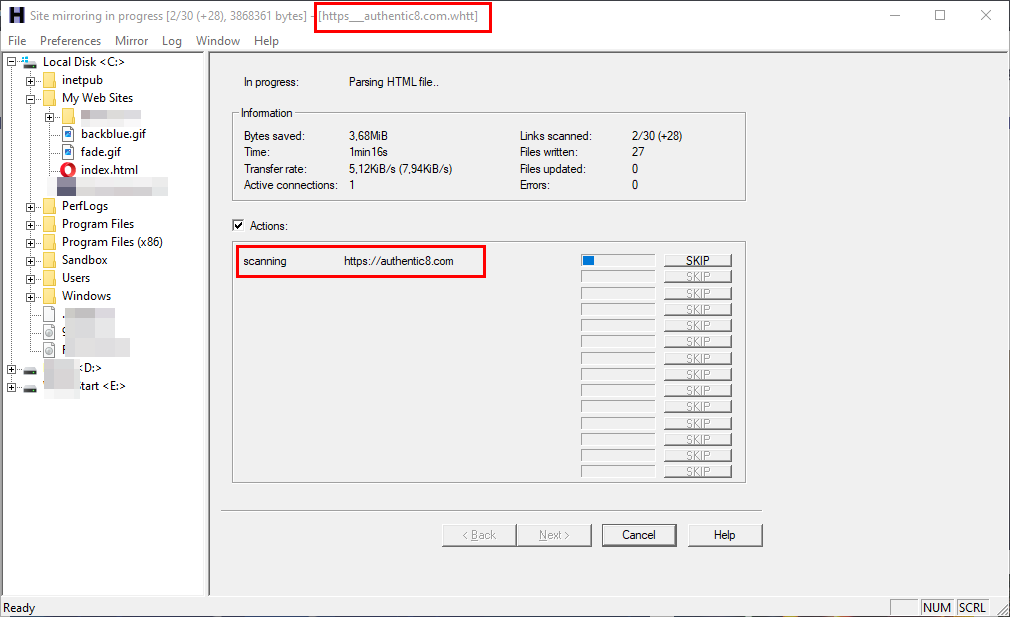
Figure 2 - Using HTTrack tool to clone any website
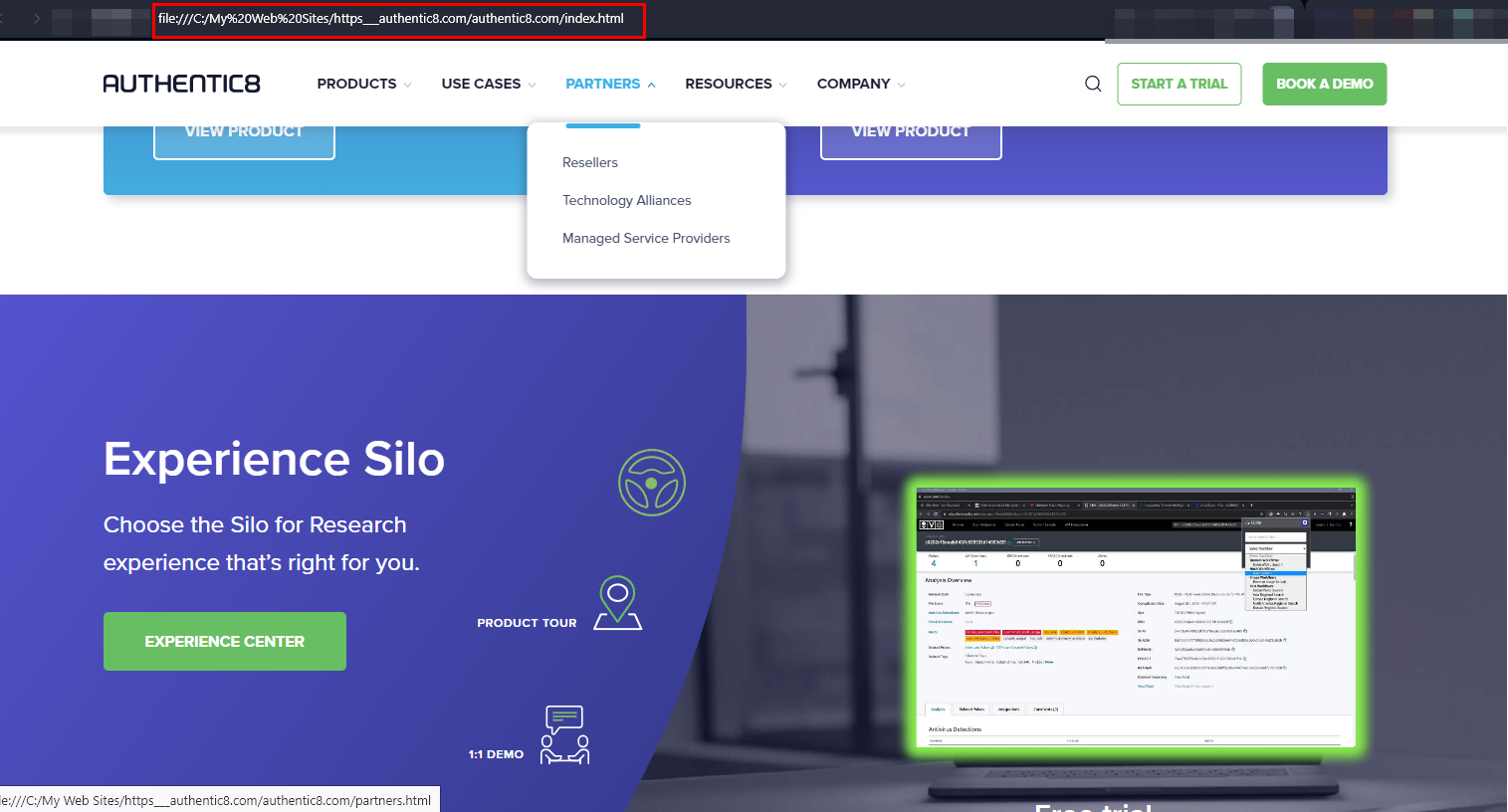
Figure 3 - Offline version of authentic8.com using the HTTrack tool. We can upload the offline version of the cloned website to a hosting space to get a complete impersonated working copy for typosquatting purposes.
After launching the typosquatting website, threat actors will wait until unsuspecting internet users accidentally misspell legitimate website addresses and finally land on their typosquatting website. Some hackers may use other tactics to drive users into their typosquatting website, such as:
- Phishing emails: Hackers send phishing emails pretending to originate from a trusted source, such as your bank, a social media provider or some popular online merchants. These emails will contain a link to the typosquatting website instead of the legitimate one.
- Malvertising: Cybercriminals may abuse legitimate online advertisement networks such as Google Ads or utilize social media advertisements to drive internet users into typosquatting websites. Some malvertising ads may contain malicious code that can redirect the user's web browser to a malicious destination once the user loads the web page containing the advertisement into their web browser.
- Search engine optimization (SEO) poisoning: Hackers leverage SEO techniques, such as keyword stuffing and link building, to try to rank their typosquatting sites higher in search engine results. This increases the chances that unaware users who mistype a URL or search for a particular website/keyword will encounter the typosquatted site instead of the legitimate one.
Now, when the unaware user visits the typosquatting website, they could be lured to provide sensitive information, such as online account credentials, financial information (banking and credit card details) or directed into installing a piece of software on their computer that contains malware (ransomware or keylogger).
How typosquatters manipulate domain names
Typosquatters utilize different tactics to manipulate domain names, such as:
Misspelling names
This is the most common method. Typosquatters register a domain name that misspells the one they intended to impersonate — for example, registering authentc8.com (the letter “i” is missing) instead of authentic8.com.
Omitting letters
In this case, typosquatters resemble the behavior of internet users when typing fast. For instance, when we type a particular domain name fast, we may end up omitting some letters from its name. For example, typing authetic8.com (missing the letter “n”) instead of authentic8.com.
Transpositions
Another error most internet users make when typing web addresses fast is to change the order of letters of the domain name — for example, typing authetnic8.com (change the location of the letter “n”) instead of authentic8.com.
Error in domain name ending
The domain name ending refers to the top-level name of the domain name, such as .com, .net, .org, .link, .ca, .us, etc. Internet users may search for a particular domain name using search engines; typosquatters could impersonate target domain names by changing the domain name suffix. For instance, we can impersonate the domain name authentic8.com by registering domain names with different endings such as: authentic8.app, authentic8.biz, authentic8.info, authentic8.co, authentic8.io, authentic8.agency, authentic8.dev, authentic8.security.
Hyphenated domains
Some domain names use hyphens to separate between two words of the domain name — for example, authentic8-store.com. An internet user may mistakenly omit the hyphen and type authentic8store.com. Typosquatters look for such name variations to hunt unaware internet users.
Alternative spellings
Some domain names may include a word that could be spelled differently in different languages. For example, here is a common list of words that are spelled differently in American English (AmE) and British English (BrE):
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
Using subdomain names
In this scenario, typosquatters employ a deceptive tactic by using a legitimate domain name as a subdomain name, leading internet users to believe they are accessing the correct website. For instance, a typosquatter might register www.authentic8.fakewebsite.com, misleading users into thinking they are visiting the legitimate website authentic8.com.
Defense strategies against typosquatting attack.
Defense against typosquatting attacks requires different strategies, such as users' cybersecurity training, proactive monitoring and using technological solutions. Here are the most important defense strategies for both users and organizations:
For organizations:
- Domain monitoring: The most critical defense strategy for website owners is to keep a close eye on new domain name registrations that use a close naming of their domain name. You can use a takedown service once you discover a domain name trying to impersonate your website. Here are some companies that provide takedown services:
- Trademark protection: Registering your brand name worldwide is critical to prevent typosquatters from impersonating your company. This allows companies to establish a legal ground to act against typosquatters. Here are some websites registering and managing trademarks worldwide:
- WIPO Madrid System – covers 130 countries
- World Intellectual Property Organization (WIPO) - global brand database
- The Trademark Clearinghouse
- Domain registration: Register all domain names that are very close to yours, such as typo-domains, different country extensions, domains with alternate spellings and variants with and without hyphens.
- SSL certificates: Your website should use an SSL certificate. In addition to providing secure connections to your website, SSL certificates provide authentication to ensure users that they are connecting to the legitimate website and not an impersonator.
- Monitor phishing attacks: If your domain name has been used in previous phishing attacks via typosquatting, such as being included in phishing emails, then it's essential to take immediate action to remove the offending domain name, as outlined earlier. You can utilize phishing threat intelligence feeds to stay informed about the latest impersonated domain names used in phishing attacks if a misspelled variation of your domain name appears in domain names blocklists:
For users:
- Ensure typing the correct web address when typing it manually in the web browser address bar or searching for it using search engines.
- Keep important websites (bank, social media services) in your web browser bookmark to ensure you access the correct domain name.
- Avoid clicking on suspicious links within emails, chat messages or private messages on social media.
- Install a reliable security solution (antivirus or antimalware) on your computing device to prevent malware downloads and to warn about malicious websites.
Navigating the modern digital landscape can be dangerous, and the growing menace of typosquatting poses a significant risk to unsuspecting internet users. By following the security precaution steps mentioned in this article, you can ensure you will not fall victim to similar attacks.
Speed up typosquatting investigations with Silo for Research
Silo for Research can help SOC teams fast-track typosquatting investigations to move quickly on takedown requests and other mitigation measures. The demo above shows how Silo:
- Keeps devices and networks isolated from malware analysts might encounter
- Automates multi-site searches to quickly gather intelligence related to the site in question
- Shows how a site presents differently based on location and other details of the digital fingerprint
Test out these features and more by starting your free trial today.


